HSBC have just hit the headlines as they’ve launched an additional layer of internet security, in th form of a calculator terminal called ‘secure key’. The calculator is small enough to attach to a key fob, and generates a random pass code each time you want to go onto online banking. This is small, but still the same irritating device that I complained about in 2007 when NatWest sent me a Xiring terminal.
Why is it so annying?
First, it forces customers to use an extra layer of security they don’t like.
Second, it adds time and challenge to online banking processes.
Third, it means people cannot access online services such as payments, if they don’t have the device with them.
Fourth, it’s just a clunky device that makes customers feel their user experience with internet banking is undermined and less secure.
I’ve never liked such things and never will, and apparently most of HSBC’s customers feel the same.
I have a solution but, before discussing solutions, let’s look in more detail at what HSBC has launched.
It’s Secure Key …

…. a small, calculator styled system.
The system is designed for two-factor authentication - a second secure code on top of a PIN or password - and using Secure Key the customer enters their PIN and then gets an OTP – One-Time Password – which is a dynamically generated random number.
This number is on top of the card PIN system, and is meant to ensure really secure internet banking. In other words, it protects the customer ... or maybe it protects the bank, as the bank is liable for customers' online banking losses.
Although the Secure Key is smaller than the similar styled systems from other banks, as it does not read the card, it still means that people need to have this with them to do most online payments activities.
That's why customers are complaining, as demonstrated above, because it’s both a hassle and potentially locks them out of their account.
As the Daily Mail puts it:
“One Financial Mail reader says HSBC told her she should use her secure key from the end of July to log in to her account, but she has never received one in the post. For the past two weeks she has been unable to access her account. Another customer, Ben Sullivan, received his device three weeks ago. Ben, from Southend, Essex, made his first attempt to use it last week but says he had to register the device first and then set it up using various ‘security questions’. To access the device Ben then had to enter a code, his date of birth and a separate PIN. ‘I'm not very pleased about it’, he says. ‘It was a lot of hassle to get it up and running.’”
Yep, it’s a pain and there's already a Facebook Community gathering to Scrap the HSBC Secure Key.
So what’s the solution?
Well I keep coming back to mobile phones.
First and most important, the mobile can be used as a Secure Key device. It's exactly the same as the pad that the banks are distributing, but it's something that youre bound to always have with you, unlike the Secure Key device.
Not only are you far more likely to have your mobile with you when you’re out and about, but the bank can geolocate you to check it’s you and your phone when a card is used, thus ensuring card and security device are held together.
Most people raise the issue of mobile security, but that's a null argument these days as, If you lose it, most people will have protected it with a mobile PIN code to start with anyway. As a result, you have two PIN entries to make - one for accessing the phone and one for the Secure Key access - before the OTP is generated.
Now to the clever bit. Phones are also rapidly becoming biometric devices.
Voice Commerce, for example, use the phone to get a voice biometric for authentication; Bank Inter use the smartphone for iris recognition; and Apple patented their finger-swipe unlock on the iPhone as a biometric last year.
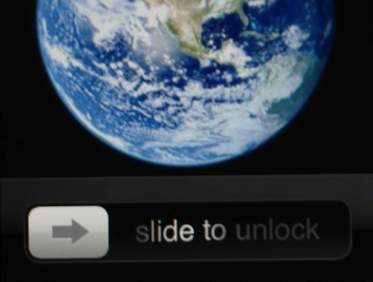
So the idea of continuing with clunky, chunky, monkey wrench solutions to online security is so last century …
Chris M Skinner
Chris Skinner is best known as an independent commentator on the financial markets through his blog, TheFinanser.com, as author of the bestselling book Digital Bank, and Chair of the European networking forum the Financial Services Club. He has been voted one of the most influential people in banking by The Financial Brand (as well as one of the best blogs), a FinTech Titan (Next Bank), one of the Fintech Leaders you need to follow (City AM, Deluxe and Jax Finance), as well as one of the Top 40 most influential people in financial technology by the Wall Street Journal's Financial News. To learn more click here...






















