The real way to crack the onboarding and criminal activity is to create strong and secure digital identities. We are moving in that direction, but it’s a long slow process. For ages now, I’ve written about getting rid of passwords and improving authentication using mobile technologies:
- Why is KYC so difficult?
- AML prevention lies in digital identities: the new form of money
- Digital identities demand a digital infrastructure
... and more.
Again, it just goes to show what a perennial subject identity is. In fact, it’s so meaty a subject that Dave Birch writes a blog about and even a whole book.
In the book, Dave suggests that the security offered by tokenisation via mobile combined with everyone building online identities via social networks will get rid of cash. I agree with him, although not necessarily on the last bit. Cashless is another huge debate. However, it is evident that the investment we are all making in our online social identities is paying off. For example, Sophos recently tracked down the gang who created the Koobface malware via their social networking activity.
Anyway, the reason I’m writing about it again is after my discussion about client onboarding and the massive overhead this creates, particularly the KYC process, for banks. There have been lots of attempts to crack this – the KYC Exchange, SWIFT’s shared KYC program, Counterparty Link and PEP databases – but nothing has succeeded so far. Now, a new alliance has been put together and, as no one knows you’re a dog on the internet, it’s called FIDO: Fast Identity Online Alliance.
FIDO (woof!) are suggesting that you should have multi-factor authentication standards using something you know (PIN, password), something you have (card, phone, token) and something you are (biometric). I came across FIDO thanks to this week’s Economist, which provides a neat summary of what it’s all about.
Looking through their website reveals some interesting ideas. For example, the mission of the FIDO Alliance is to change the nature of online authentication by:
- Developing technical specifications that define an open, scalable, interoperable set of mechanisms that reduce the reliance on passwords to authenticate users.
- Operating industry programs to help ensure successful worldwide adoption of the Specifications.
- Submitting mature technical Specification(s) to recognized standards development organization(s) for formal standardization.
The origins of the FIDO Alliance go back over eight years, and were prompted by PayPal’s frustrations with multifactor authentication. The issue is that additional security keys increase security but also irritate the user. How do you get around that?
By creating a new standard, the characteristics of which would include:
- a general purpose authentication standard, not just confined to fingerprint biometrics, or even just biometrics,
- a considerable commercial element in play — that an ecosystem would have to be bootstrapped in order for this idea to become successful, requiring tight coordination between supply and demand,
- a new organization to write this new technical standard, applying best practices from other such organizations.
All well and good, and they’ve got Google, Bank of America, Samsung, PayPal, MasterCard, Microsoft, Lenovo, Visa and more in the mix to develop this new standard.
It all sounds so wonderful.
But then I read what the new standard is all about and sat there afterwards feeling a little disappointed. This new alliance has developed two standards y’see. One is a passwordless standard and the other is a multifactor authentication.

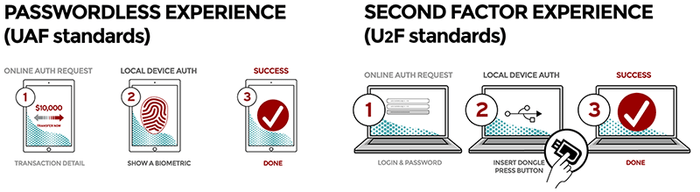
Passwordless UX (UAF)
- User carries client device with UAF stack installed
- User presents a local biometric or PIN
- Website can choose whether to retain password
The passwordless FIDO experience is supported by the Universal Authentication Framework (UAF) protocol. In this experience, the user registers their device to the online service by selecting a local authentication mechanism such as swiping a finger, looking at the camera, speaking into the mic, entering a PIN, etc. The UAF protocol allows the service to select which mechanisms are presented to the user.
Once registered, the user simply repeats the local authentication action whenever they need to authenticate to the service. The user no longer needs to enter their password when authenticating from that device. UAF also allows experiences that combine multiple authentication mechanisms such as fingerprint + PIN.
Second Factor UX (U2F)
- User carries U2F device with built-in support in web browsers
- User presents U2F device
- Website can simplify password (e.g. – 4 digit pin)
The second factor FIDO experience is supported by the Universal Second Factor (U2F) protocol. This experience allows online services to augment the security of their existing password infrastructure by adding a strong second factor to user login. The user logs in with a username and password as before. The service can also prompt the user to present a second factor device at any time it chooses. The strong second factor allows the service to simplify its passwords (e.g. 4–digit PIN) without compromising security.
During registration and authentication, the user presents the second factor by simply pressing a button on a USB device or tapping over NFC. The user can use their FIDO U2F device across all online services that support the protocol leveraging built–in support in web browsers.
So, on the one hand, I applaud this alliance for actually trying to do something. What they've achieved so far seems laudable, and is based upon what can be achieved using current state technologies. But, on the other hand, my disappointment is that it does not lay out a vision for a future state. In fact, the challenge with the two standards outlined is that, in both cases, the new standard involves the user doing something. They either have to plug in a dongle, enter a PIN, stick their finger onto a device or something like that. And my disappointment is that I really want a digital identity that involves me doing nothing.
I’ve already blogged about this recently Why the blockchain will radically alter our futures - FIDO doesn't mention the blockchain - and I honestly do not believe that in ten years’ time, we will be actively authenticating our identities. It will be automatic and sensed.
So the FIDO Alliance is a good thing for now, but it appears to be addressing the online identity issues with standards of the past rather than the future. Where’s the new standard for an online identity that has some vision?
Chris M Skinner
Chris Skinner is best known as an independent commentator on the financial markets through his blog, TheFinanser.com, as author of the bestselling book Digital Bank, and Chair of the European networking forum the Financial Services Club. He has been voted one of the most influential people in banking by The Financial Brand (as well as one of the best blogs), a FinTech Titan (Next Bank), one of the Fintech Leaders you need to follow (City AM, Deluxe and Jax Finance), as well as one of the Top 40 most influential people in financial technology by the Wall Street Journal's Financial News. To learn more click here...

