Growing up in 21st century is wondrous, amazing
and fun.
You can connect to everyone on the planet.
You can find friends from Tokyo to Timbuktu.
You can catch an airplane like your dad caught a bus.
You can pay carry a roomful of music around in your pocket
and watch movies through the air.
You can even pay for things without paper!
Wow!
Hasn’t the world changed a lot?
And yes, it’s going to change a whole lot more as everything
becomes wirelessly connected.
But there’s a flaw to all of this.
And the flaw is humanity.
Humanity is going to screw up our wirelessly connected
planet.
Humanity is going to rebel against the assault of
technology.
Why?
Because the technology is messing up our lives.
You are no longer able to keep anything secret.
You do something at university that becomes a huge hit on facebook
… then you apply for a job four years later and they say, “aren’t you the guy
on facebook?”
You create a viral for youtube about what’s in your
underwear … and you get a brown envelope the following day at work with your
severance papers.
Even criminals are not immune to this assault.
I was listening to a presentation from Sophos the other day
and they told this wonderful story about catching cybercriminals.
The story is legend and is how Sophos tracked down the
Koobface gang.
It’s a long story (27 page PDF download), but here’s my summary.
Koobface (an anagram of “Facebook”) is malware
that spreads via social networking sites, infecting PCs and builds a botnet of
compromised computers. It is so sophisticated it can even create its own social
networking accounts, so that it can aggressively post links helping it to
spread further.
This particular botnet does not steal financial information,
but it does download pay-to-download software and hijacks search queries in
order to find specific pay-to-display adverts.
The thing is that cybercriminals aren’t that cute, and the
Koobface gang made a big mistake.
Reading the Sophos report makes for interesting
understanding.
A major breakthrough came in December 2009 when the Webalizer
statistics tool showed an unusual request to a file named “last.tar.bz2,” which
turned out to contain a full daily backup of the Koobface Command & Control
software.
Within these backups, two things were found that gave away
who the gang were.
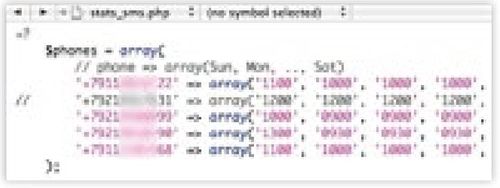
First, a PHP script which was used to submit daily revenue
statistics via short text messages to five mobile phones. Unfortunately for the
gang, this script included their international prefix +7 identifiers, showing that
this was being transmitted to Russian telephone numbers.

There was also an image found within one of the backups.
This picture is completely unrelated to the function of the Koobface botnet, but
appeared to have been placed there by a Koobface gang member.
What the gang member may not have known is that, unless you
turn off location functions, every iPhone picture carries with it metadata that
provides the geolocation of where the photograph was taken and, according to
the metadata contained within this photo, it was taken with an Apple iPhone with
a Latitude of N 59° 55.66' and a Longitude of E 30° 22.11'. This directly
points to the centre of St. Petersburg, Russia.
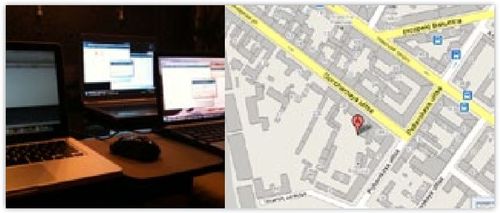
The Sophos investigrators then used this information to
start searching for any digital footprint related to these telephone numbers in
St. Petersburg, and found that one of them was selling a BMW on an online car
auction website, albeit with the number plate hidden.
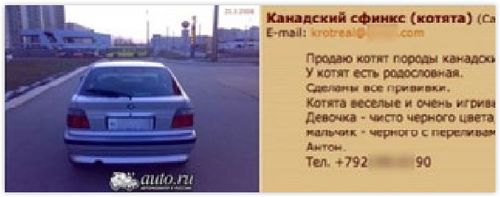
The same telephone number was also being used to try to sell
some lovely fluffy little kittens.
Yes, even criminals like cats.
Trouble is that the gang member has now given an email
address: krotreal@****.com. Although the website domain was hidden, the investigation
discovered the name Krotreal was his
handle on various websites including Flickr, Netlog, LiveJournal, vkontakte.ru,
YouTube, FourSquare, Twitter and more.
This then provided a goldmine of personal information, such as the full
number plate for that BMW that was up for sale.
This was a picture on Flickr accompanied by the caption “My little
beauty :)”:

Aha! Now that the investigators
had got hold of the number plate of Krotreal, they also had the name and telephone
number of the German car-dealer who sold the car, and used that to trace the chain
of ownership for the car from that dealer to its current Russian owner.
All well and good, but not enough to get an indictment or
conviction for spreading Koobface malware around the world.
So the investigators delved into vkontakte, facebook,
twitter and more, and eventually found a reference to Krotreal being the owner
of an adult website allcelebrity.ru.
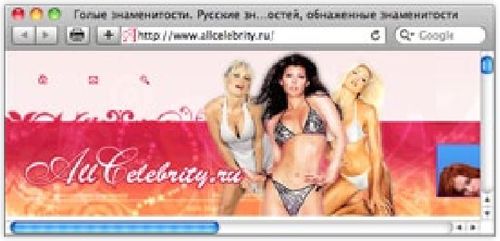
Every website is logged with ownership information, and this
website was registered by Krotreal@mobsoft.com.
Surprisingly the Whois details of the
website had not been concealed (it is now) and also showed that an Anton K. was the owner,
with a St. Petersburg telephone number.
The team now had a name and full email address, and found
that MobSoft.com rented offices on the top floor of this St. Petersburg
building.

Companies usually need to be registered with the government
or the tax service and fall under specific legislation mandating reports. They usually keep public websites providing
information about their history and the former and current management. This is now making life interesting as a
suspect who is the owner or shareholder of a company is easier to find as they
are more likely to have filed valid identity information during the company
registration processes.
Investigating in depth, the Sophos team found that registered
persons were listed for MobSoft, or МобСофт in Cyrillic, and the details
included dates of birth and passport ID number confirming that one of the
owners was Anton K.
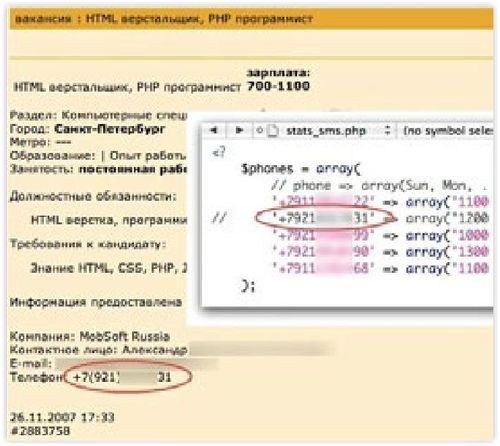
Upon further searches about the company, the team also found
a job advert listing another contact.
This time it is an Alexander K. with a telephone number that also was
found on the original list of numbers in the PHP script.
Searching in a similar fashion to the searches made about
Anton K., the researchers discovered that Alexander K. was also commenting on
various vkontakte.ru walls under various nicknames including “floppy”, “megafloppy”
and “darkfloppy” (vkontakte is a
Russian version of facebook). This led
the investigators to identify another potential gang member, Roman K.
At this point howevr, the trail began to run cold and trying various avenues, most reached a dead end.
That was until the team hit upon Maria K.
Maria K. was listed as a co-owner of one of the MobSoft companies
and luckily her vkontakte profile gave full public access.
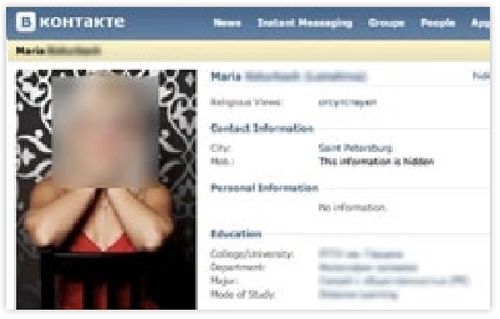
Her profile not only gave the team access to a list of all
of her friends but also many tagged photos of them. They found that not only was Roman
K. on her friend list, but that Maria and Roman K. were married with a daughter.

They also found that the family spent their holidays with
Anton K., suggesting a fairly close relationship between them. The links also led them to identify two more
gang members: Syvatoslav P., and Stanislav A.
A painstaking research project, with most of the information
showing that social networking is just as dangerous for a cybercriminal as it
is for an honest citizen.
Sophos eventually handed all their research on the gang to
law enforcement authorities … but no charges have been brought to date because,
as with all cybercrime, when the victims are in one country, the servers in another
rand the perpetrators in a third, it’s pretty hard to get any indictment.
Shame.
But I recount the story as this is a corollary of one I
wrote up a while ago about Aaron Barr, former head of cybersecurity at America’s
leading digital security company HBGary.
And you can also read the whole story about the Koobface sting at
the Sophos Website.
Oh, and just to finish off, here’s the Koobface gang’s
annual holiday snaps.

Nice!
Chris M Skinner
Chris Skinner is best known as an independent commentator on the financial markets through his blog, TheFinanser.com, as author of the bestselling book Digital Bank, and Chair of the European networking forum the Financial Services Club. He has been voted one of the most influential people in banking by The Financial Brand (as well as one of the best blogs), a FinTech Titan (Next Bank), one of the Fintech Leaders you need to follow (City AM, Deluxe and Jax Finance), as well as one of the Top 40 most influential people in financial technology by the Wall Street Journal's Financial News. To learn more click here...

