In recent days, I’ve discovered a lot of theorems and ideas in digital areas where, when you integrate finance and technology, you realise that you are living in a world of rocket science thinking. For example, I am spending a lot of time talking with experts about digital identity and trust, as that’s the theme of my next book. It’s interesting as there are so many ideas but few solutions.
Obviously, the use of usernames and passwords no longer work anymore, but what is the alternative? Biometrics helps and you can also add SSL (Secondary Security Layers) and OTPs (One Time Passwords), but the digital identity system is busted.
When I logon these days, so many websites ask for an authenticator code from an authenticator app or a passkey, as an addition to all the other entry requirements, that you just feel like giving up.
So, what is the solution?
Well, it is developing around several key concepts which, as with all things finance and digital, are wrapped up in confusing acronyms. Here is my simple guide:
Zero Knowledge Proof (ZKP)
This is where you give a view of your digital identity, but do not release the whole identity. The concept is similar to Where’s Wally, where you have to find Wally in a picture. ZKP shows Wally in your identity picture, but keeps the rest under wraps. In other words, you see the bit you need to know but only the bit you need to know. The rest is kept private.
Sounds good, but then there is a related idea called zero trust. It is related but different.
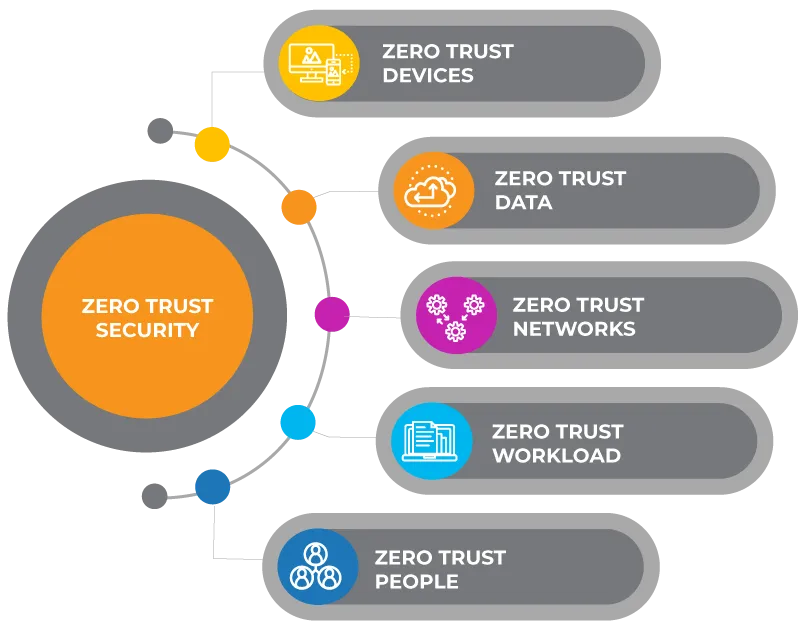
Zero Trust
Zero trust, unlike Zero Knowledge Proof, does not accept any device or access without verification. In other words you might reveal where Wally is in your identity profile, but I still don’t trust that it’s you without a verification. In addition, I don’t trust your device, system, platform, profile or any other aspect of who you are until you verify. This approach to security means that you cannot access anything until your identity and device that you are using is fully authenticated, identified and been verified. It is pretty much the approach used by many today.
Source: Sumit K
The thing is that ZKP and Zero Trust are used for access but then, behind the scenes, are several other major concepts such as Multi-Sig, ADCs and CESR. What?
Multi-Signature (Multi-Sig)
Multi-Signature (Multi-Sig) is a security feature used mainly with cryptocurrency transactions and requires multiple keys to authorise anything. In other words, you may have already enabled access, but you need further proofs to make a transaction. Whilst it may be annoying, it adds extra layers of security and a Multi-Sig is kind of in the round, as in you have to have several verifiers – not just one or two – to make anything happen. The more signatures required, the more secure the transaction.
Authentic Data Chain Containers (ADCs)
ADCs are data structures used to create a chain of verified authorship and provenance for data. The aim is to link everything so it can be track and traced from source to outcome. They function by linking putting data into containers and the containers are then linked together in a verifiable chain, similar to a chain-of-custody, demonstrating a history of how the data was created and who authored it.
Then you have CESR.
Composable Event Streaming Representation (CESR)
Now we are getting into the core of blockchain technologies and it gets pretty detailed. If I am honest, at this point, it is getting far too technical for me to even keep up. Therefore, if you want to understand this in-depth, there si a great blog by Henk Van Cann that explains the whole thing, but my take away is that CESR is a way of connecting data so that it cannot lose its authenticity and, more importantly, can combine text and data.
Whilst ZKP and Zero Trust can help in the access to digital services, secure attribution is another concept focused upon the defence of digital services.
Secure attribution
Secure attribution is the process to identify and assign responsibility for any digital attacks. This concept aims to find any specific individuals, groups, or organisations involved in a hack. It involves investigating the attack, analysing their digital footprints, and gathering evidence to determine the perpetrator's identity and motivations. This process is crucial for incident response, threat intelligence, and potential legal action against the attacker.
This gets really technical and could lead me down into Schrödinger’s Cat, Fibonacci trading, Black Scholes, Goldbach’s Conjecture, the Riemann Hypothesis, the Rule of 40, Fermat’s Last Theorem and more.
Let’s not go there.
Chris M Skinner
Chris Skinner is best known as an independent commentator on the financial markets through his blog, TheFinanser.com, as author of the bestselling book Digital Bank, and Chair of the European networking forum the Financial Services Club. He has been voted one of the most influential people in banking by The Financial Brand (as well as one of the best blogs), a FinTech Titan (Next Bank), one of the Fintech Leaders you need to follow (City AM, Deluxe and Jax Finance), as well as one of the Top 40 most influential people in financial technology by the Wall Street Journal's Financial News. To learn more click here...